A Comparative Analysis of Security Algorithms and Mechanisms for Protecting Data, Applications, and Services During Cloud Migration
Main Article Content
Abstract
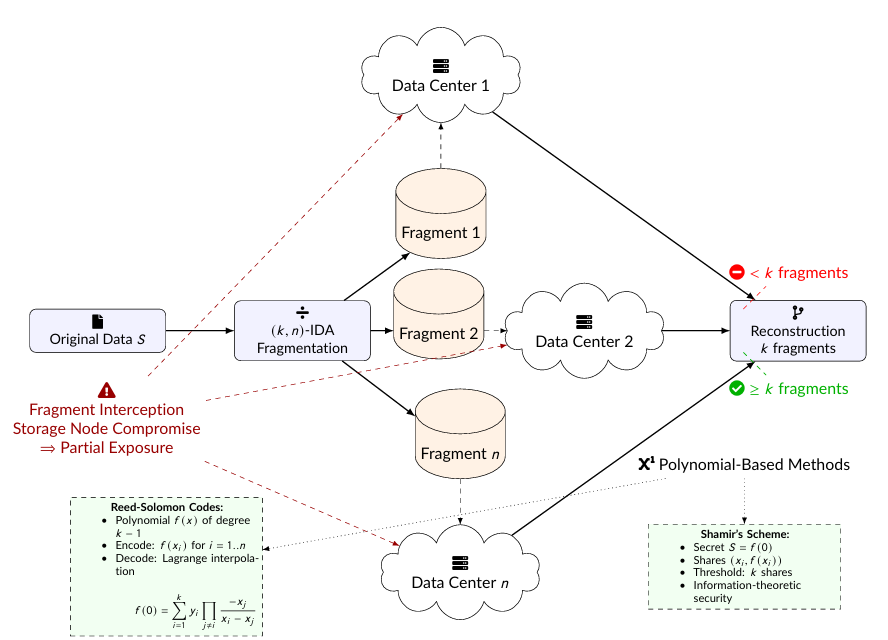
Migrating critical data, applications, and services to cloud-based infrastructures introduces numerous security challenges that require robust, technically sound solutions. This paper presents an in-depth, technical comparative analysis of algorithmic strategies crucial to securing cloud migration processes. We investigate three primary cryptographic algorithm categories—symmetric-key, asymmetric-key, and hashing algorithms—and detail their underlying mathematical constructs, operational mechanisms, and computational complexities. In addition to encryption techniques, the study examines data masking and obfuscation methods that protect sensitive information without altering data structure, and information dispersal algorithms (IDAs) that use erasure coding and secret-sharing principles to fragment and distribute data securely across heterogeneous cloud nodes.This study elucidates the trade-offs between computational overhead, latency, and security robustness by integrating formal descriptions, algorithms, and performance benchmarks. The analysis demonstrates that while symmetric-key algorithms (e.g., AES) offer high throughput due to their low algorithmic complexity—typically \(O(n)\) for block processing—their key distribution problem necessitates the use of computationally intensive asymmetric-key schemes (e.g., RSA, ECC) for secure key exchange. Hashing algorithms, built on the Merkle-Damgård construction or sponge functions, provide integrity guarantees but lack confidentiality. This research further discusses how hybrid approaches and multi-layered security architectures can be orchestrated to meet strict compliance and performance requirements. This paper provides an outline for evaluating and implementing algorithmic solutions to secure cloud migration, with implications for both theory and practice.