Architectures for AI Integration in Next-Generation Cloud Infrastructure, Development, Security, and Management
Main Article Content
Abstract
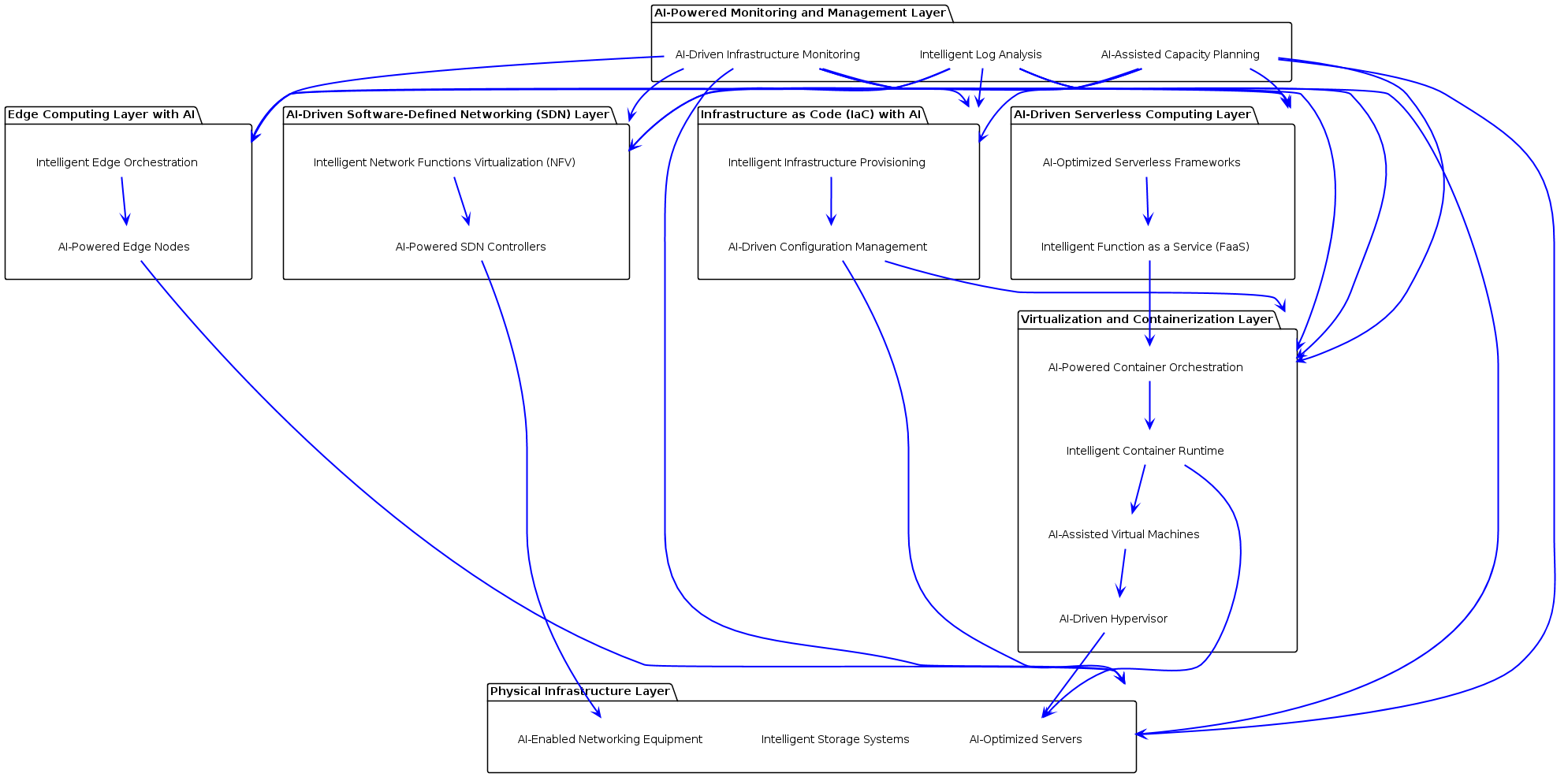
The rapid advancement of artificial intelligence (AI) technologies has opened new possibilities for enhancing the capabilities of next-generation cloud computing. This research discusses the applications of AI in four key categories of cloud computing technologies: infrastructure and virtualization, application development and deployment, security and compliance, and cloud management and optimization. The study presents architectures for each category, detailing the components and their interconnected dependencies. In the infrastructure and virtualization, AI techniques are employed for resource allocation, edge computing, container orchestration, network optimization, and automated infrastructure management. For application development and deployment, AI assists in microservices design, scaling and management of cloud-native applications, DevOps processes, workload balancing, and low-code/no-code platforms. Security and compliance benefit from AI-powered threat detection, identity and access management, encryption key management, automated compliance checks, and fraud detection in blockchain transactions. Cloud management and optimization uses AI for cost optimization, workload migration, autoscaling, performance monitoring, and disaster recovery planning. The architectures showcase the integration of AI algorithms and tools within each layer of the cloud computing stack. The study highlights the dependencies between components, emphasizing the need for an all-embracing approach when implementing AI in cloud environments. This research aims to provides basis for further exploration and development of AI-driven cloud computing solutions.