Implementing Encryption and Cybersecurity Strategies across Client, Communication, Response Generation, and Database Modules in E-Commerce Conversational AI Systems
Main Article Content
Abstract
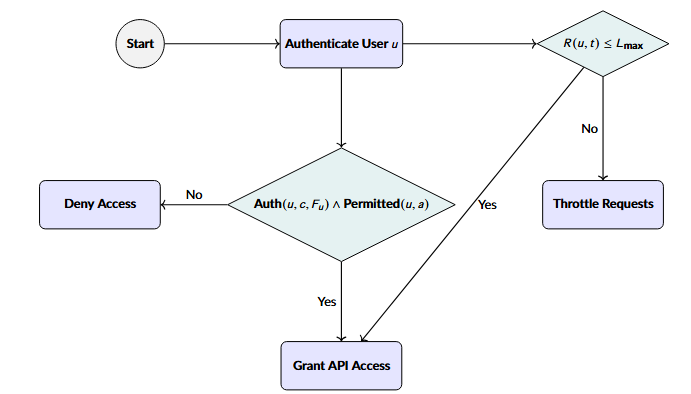
The integration of conversational AI into e-commerce enables better customer service and personalization of shopping experiences. This advancement in technology has also warranted the focus of a number of important concerns regarding security, such as sensitive user data protection and protection of transaction information. This paper will be proposing a systematic architecture model for securing conversational AI systems in an e-commerce domain through encryption techniques in tandem with adherence to cybersecurity practices. This model contains four major modules: \textit{client module, communication module, response generation module, and database module}. In this, the client module uses strict authentication mechanisms for access. Even multi-factor authentication can be used for the same. The coding should be done in such a way to avoid as many vulnerabilities as possible, including injection attacks, by using secure coding practices. The communication module should implement secure data transmission protocols like TLS. This module is integrated with rate limiting to defend against Denial of Service attacks. The security features are integrated inside the AI engine through adversarial training with Differential Privacy in the Response Generation module, serving to reduce risks related to data leakage and manipulation. This involves access control so as to provide mechanisms against unauthorized use of functions. Data encryption in the database is at rest using algorithms like Advanced Encryption Standard, or AES, for secure data storage. Besides, the foundation for access control is the principle of least privilege; monitoring provides an added capability for the detection of unauthorized attempts at access. The model also formalizes definitions of security functions and properties to represent authentication, encryption, and access control mechanisms. The proposed model will further advance the design of secure AI systems with a practical framework that can be adapted for real-world e-commerce applications, with the aim of reaching data protection standards and improving user trust.